
Just got a coronavirus-related email from an unfamiliar sender? Odds are they are trying to steal money and/or data from you, security experts say.
Before COVID-19, FBI’s Crime Complaint Center (IC3) was receiving roughly 1,000 cybersecurity complaints a day. That number rose to between 3,000 and 4,000 daily instances since the pandemic began.
The uptick coincided with the start of teleworking. Cybercriminals are increasingly targeting work-at-home employees, hoping that some companies may not have properly secured their infrastructure or trained their personnel. The goal is to gain control of corporate networks through remote access and to steal sensitive data.
Criminals often trick their victims into clicking malicious links or downloading malware by posing as government/health authorities, offering too-good-to-be-true Covid-related deals, or spreading misinformation disguised as important news about the virus.
INTERPOL’s private sector partners detected 907,000 spam messages, 737 incidents related to malware, and 48,000 malicious URLs — all related to COVID-19 — between January and April 2020.
Who is the prime target?
Healthcare providers, banks, and government organizations have been hackers’ top targets in the pandemic.
According to data by VMware’s Carbon Black, almost one third of all cyberattacks in the US (27%) are directed at either healthcare facilities or banks.
The World Health Organization (WHO) and the US Department of Health and Human Services (HHS) were targeted by hackers during the first few months of the health crisis.
Tonya Ugoretz of the FBI says that many threat actors are from nation-states that want to “gain insight into COVID-19-related research.”
Countries have a very high interest in information on the virus… such as information on a vaccine. We have certainly seen reconnaissance activity and some intrusions into some of those institutions, especially those who have identified themselves as working on COVID research.
There was also a 238% surge in cyberattacks against banks between February and April last year, reports VMware’s Carbon Black.
At the same time, hacking of state and local governments in the US rose by about 50%.
The cost
The impact from a cyberattack can range from the financial cost of a breach, data loss, potential financial misstatement, disclosure obligations, and legal and regulatory actions to reputational damage. Some attacks are specifically aimed at revealing regulatory compliance issues, and hackers may demand ransom if they find any.
According to a whitepaper by the Anti-Fraud Collaboration, the global average cost of a data breach was $3.86 million in 2020. The US has the highest figure among world countries at $8.64 million. If we look at the data breakdown by industry, we’ll see that healthcare, financial, and pharmaceutical industries have some of the highest data breach costs. That’s probably the reason they get attacked the most – hackers hope that companies in these sectors will pay up.
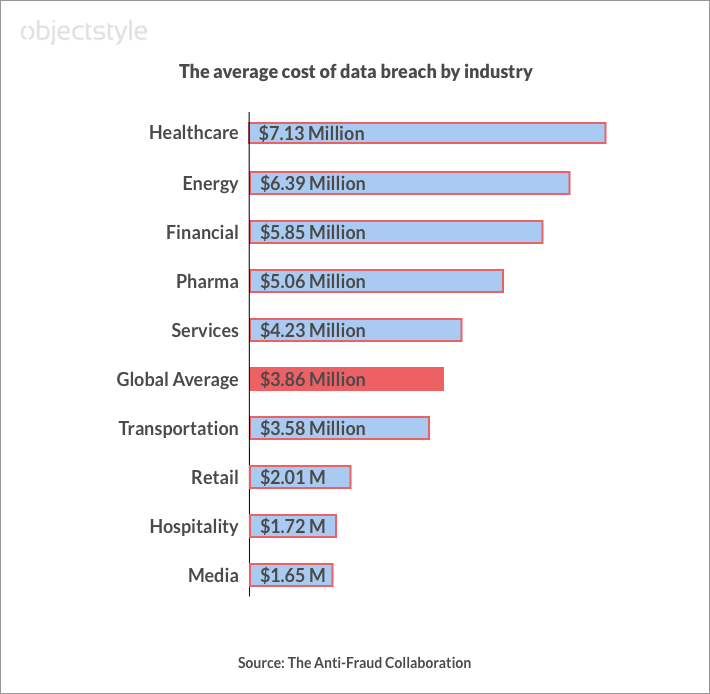
In the U.S. alone, security company Emsisoft estimates the cost of ransomware attacks last year to be over $9 billion between ransoms paid and downtime/recovery.
In another report, the government in North Rhine-Westphalia (NRW), a province in Germany, may have lost between $34 million to $109 million to fraudsters who posed as legitimate citizens eligible for government aid during the health crisis.
Popular attack types
In a report by VMware’s Carbon Black, 82% of CIOs said that threat actors’ techniques have become more sophisticated. Hackers now often use social engineering and advanced multi-step phishing tactics to get to their end-target.
Here are some popular Covid-19 phishing themes:
- Emails from national or global health authorities (e.g., “updated coronavirus cases near you”).
- Government orders and financial support initiatives (e.g. INTERPOL partner Kaspersky uncovered a scheme in which hackers used a COVID-19 tax rebate to entice recipients to enter their financial and tax information on a fraudulent website set up specifically for this purpose).
- Fake payment requests and money reimbursements.
- Coronavirus-related charity and donation requests (e.g., donations to stop the spread of the virus and asking recipients to donate using Bitcoin).
- Investments and stock offers.
- Offers of vaccine and medical supplies.
- False medical advice and “magic” cures.
- Other types of misinformation (e.g., conspiracy theories, too-good-to-be-true offers like free food and large discounts at supermarkets).
- COVID-19 tracking apps for mobile phones.
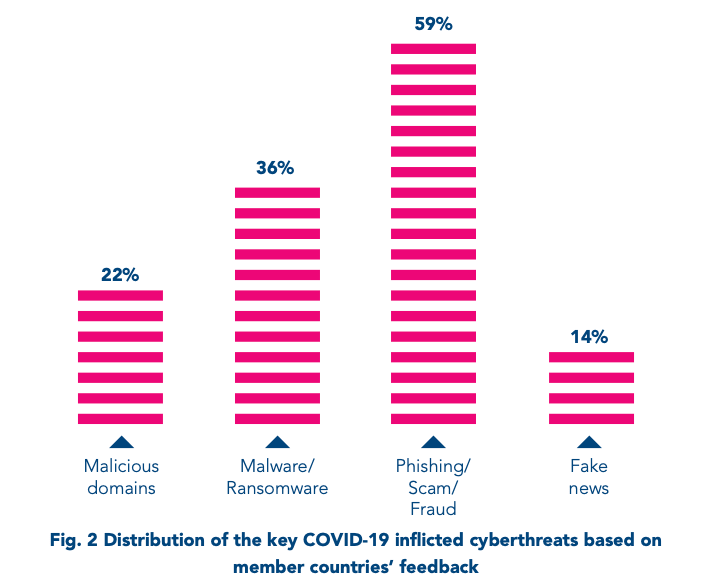
Alongside phishing, other threats include:
- Hidden malware (Many malicious emails directed victims to educational or health-related websites riddled with malware. E.g., there could have been a coronavirus map loaded from a legitimate source that ran malware in the background when clicked).
- Malicious domains (Domains that contain words like “coronavirus” or “covid-19”. These domains are used to carry out the above-mentioned malicious activities. From February to March 2020, INTERPOL found a 569% increase in malicious registrations, including malware and phishing, and a 788% uptick in high-risk registrations).
- Business email compromise, or BEC (INTERPOL warns that BEC continues to be the scheme-of-choice for many cybercriminals. BEC consists in sending legitimate-looking money transfer requests, invoices, and similar documents, while impersonating a company and its employee by using a compromised or a slightly modified email address. In the pandemic, BEC campaigns often target vulnerable industries: manufacturing, finance, pharmaceuticals, healthcare, and transportation. The pressure to procure essential supplies and healthcare products makes people lower their guard and overlook the red flags in such requests).
Keeping your data secure – recommendations
What can companies and individual employees do to protect themselves from cyber thieves? Here is a (pretty much exhaustive) list of recommendations:
- Do not download attachments from email addresses you do not recognise.
- Do not click suspicious links (that you find in questionable emails).
- Keep your operating systems and apps updated.
- Use strong passwords, keep them secure, and update them regularly.
- Use strong anti-virus software and keep it up to date.
- Enable two-step authentication, if possible.
- Do not publicly disclose data that can be used to guess your password or answer security questions – for example, your date of birth, your first pet’s name, etc.
- In a business setting, pay attention to slight differences in the sender’s email address like [email protected] vs. [email protected].
- Verify any payment request in person, if possible.
- Be wary if the sender is pressing you to wire the funds quickly.
- When working from home, make sure your WiFi network is protected by a strong password. Avoid using easy-to-guess passwords like 12345.
- Use only trustworthy third-party communication channels like messengers, chat software, video conferencing software, etc. to share data within the company.
- To prevent data loss (in case your data is taken hostage), back up important files and store them independently from your system.
In conclusion
Security experts warn that when COVID-19 vaccination begins and as vaccines become more widely available, there will be another spike in phishing activities. And it may be underway as you are reading this post.
And, while it’s always good to #washyourcyberhands and stay vigilant while keeping your digital business environment secure, it is especially important now during the pandemic.
Related Blogs

Securing PII in a software system
LEARN MORE